Open CCS > click 'Tasks' > 'Advanced Tasks' > 'View Logs'
- CCS logs all events generated by the antivirus, firewall, HIPS, containment, Data Loss Prevention (DLP) and other modules.
- The 'Log Viewer' lets you view logs from any selected module
- You can filter logs to view only the events that involve selected activities or events generated within a certain period of time
- You can also save logs as an HTML file
Use the following links to jump to the task you need help with:
Open the log viewer module
There are three ways to open the log viewer:
- Click 'Logs' in the CCS menu bar:
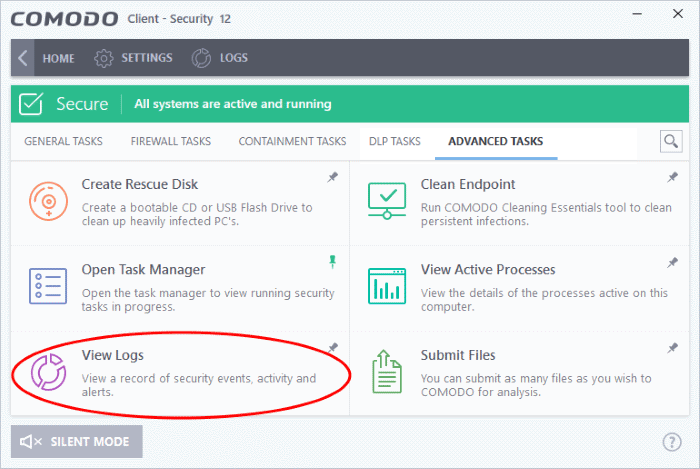
2. Click 'Tasks' on the CCS home screen then 'Advanced Tasks' > 'View Logs':
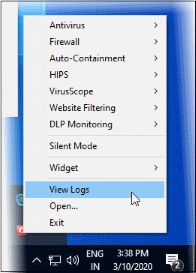
3. Right-click on the CCS tray icon then select 'View Logs':
The log dashboard shows a summary of events on the endpoint:
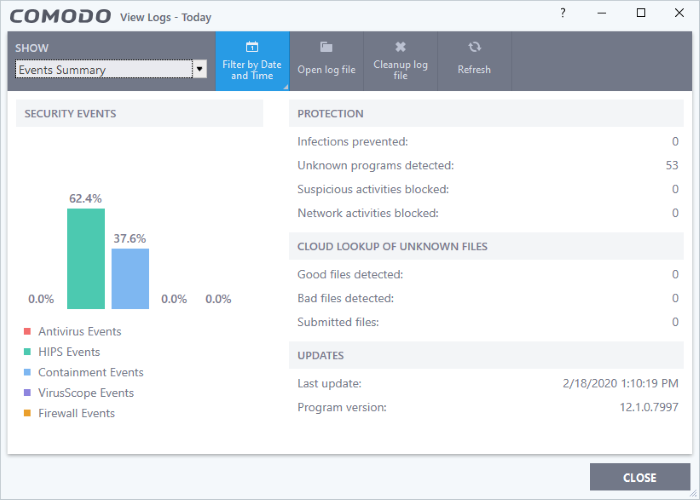
- Use the drop-down at top-left to view a specific type of log:
The controls the top lets you execute the following actions:
- Advanced Filters – Use the filters to view events generated by selected activities
- Filter by date and time – Use the filters to view the events occurred within a selected time period
- Export - Save the logs as an HTML file. You can also right-click inside the log viewer and choose 'Export'.
- Open log file - Browse to and view a saved log file.
- Cleanup log file - Delete the selected event log
- Refresh - Reload the current list and show the latest logs
Antivirus
- Click 'Logs' in the CCS menu bar
- Select 'Antivirus Events' from the drop-down at upper-left
Antivirus logs contain stats about scanned objects, the settings used for each task, and a history of actions performed on individual files. Logs are recorded for real-time protection events, antivirus database updates and more.
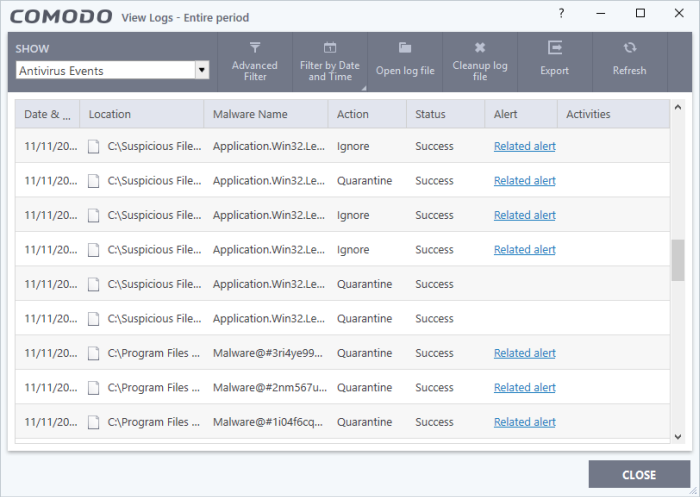
Date & Time - When the event occurred.
Location - The installation path of the suspicious application
Malware Name - The malicious item that was detected
Action - How the malware was handled by CCS.
Status - Whether the action taken was a success or failure
Alert - Click 'Related Alert' to view the notification generated by the event
- Click any column header to sort the entries in ascending \ descending order
- Use the 'Advanced filter' option to search for specific events
- Use the 'Filter by time' option to view the events occurred within a selected period of time
- Click 'Export' to save the logs as HTML file
VirusScope
- Click 'Logs' in the CCS menu bar
- Select 'VirusScope Events' from the drop-down at upper-left
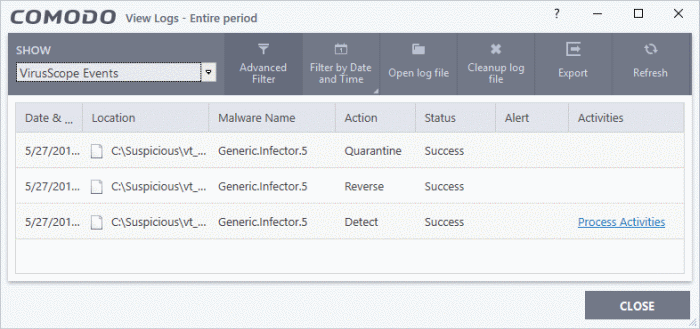
Date & Time - When the event occurred.
Location - The installation path of the suspicious application
Malware Name - The malicious item that was detected
Action - How VirusScope handled the malware.
- Reverse - VirusScope attempted to undo any changes made by the malicious item
- Quarantine - VirusScope placed the suspicious file in quarantine
- Detect - VirusScope observed malicious activity but did not quarantine the file or reverse its changes
- Ask - VirusScope detected malicious activity and showed an alert. The alert asks whether you want to quarantine the file or reverse its changes
Status - Whether the action taken was a success or failure
Alert - Click 'Related Alert' to view the notification generated by the event
Activities - Click 'Related Alert' to view the notification generated by the event. An example is shown below:

- Click any column header to sort the entries in ascending \ descending order
Firewall
- Click 'Logs' in the CCS menu bar
- Select 'Firewall Events' from the drop-down at upper-left
Firewall events are created for various reasons. Reasons include when a process attempts a connection that breaks a firewall rule, or when there is a change in firewall settings.
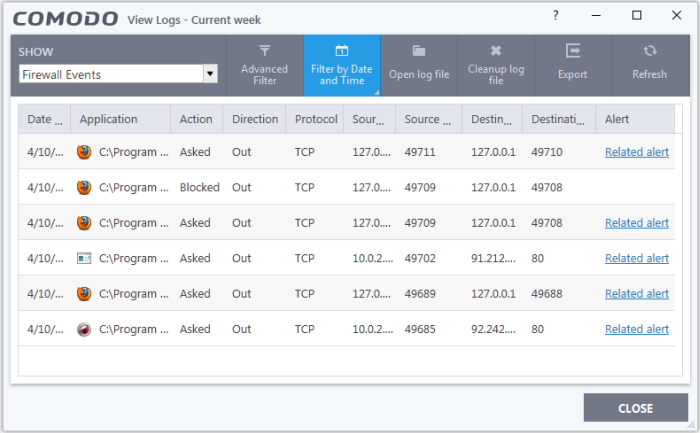
Date & Time - When the event occurred.
Application - The name of the program or process that caused the event.
Action - How the firewall reacted to the connection attempt. For example, whether the attempt was allowed, blocked o r an alert displayed.
Direction - Whether the connection attempt was inbound or outbound.
Protocol - The connection method that the application attempted to use. This is usually TCP/IP, UDP or ICMP, which are the most heavily used networking protocols.
Source IP - The address of the host from which the connection attempt was made. For outbound connections, this is usually the IP address of your computer. For inbound connections, it is usually the IP address of the external server.
Source Port - The port number that the source host used to make the connection attempt
Destination IP - The address of the host to which the connection attempt was made. For inbound connections, this is usually the IP address of your computer.
Destination Port - The port number on the destination host which the source tried to connect to.
Alert - Click 'Related Alert' to view the notification generated by the event
- Click any column header to sort the entries in ascending \ descending order
HIPS
- Click 'Logs' in the CCS menu bar
- Select 'HIPS Events' from the drop-down at upper-left
Host intrusion prevention (HIPS) events are generated for various security reasons. These include changes in HIPS settings, or when an application tries to access a restricted area, or when an action contravenes your HIPS rulesets.
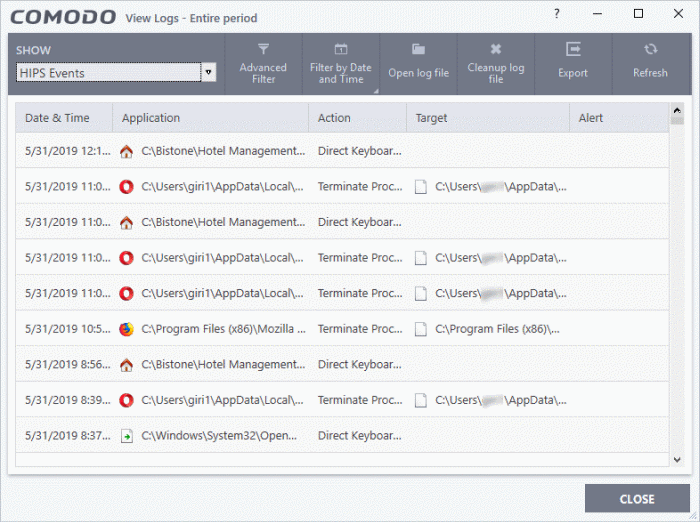
Date & Time - When the event occurred.
Application - The name of the program or process that caused the event.
Action - The activity of the application and how HIPS handled it
- If the action was allowed to proceed then this column will show the result of that action.
- Click the 'Related Alert' link to see the notification that was shown at the time.
- This column will state 'Block File' if the action was not allowed.
Target - Location of the file, COM interface or registry key accessed by the process.
Alert - Click 'Related Alert' to view the notification generated by the event
- Click any column header to sort the entries in ascending \ descending order
Containment
- Click 'Logs' in the CCS menu bar
- Select 'Containment Events' from the drop-down at upper-left
CCS records all actions taken by the containment module. Events that are recorded include:
- When you manually run an application in the container
- When an auto-containment rule runs an application in the container
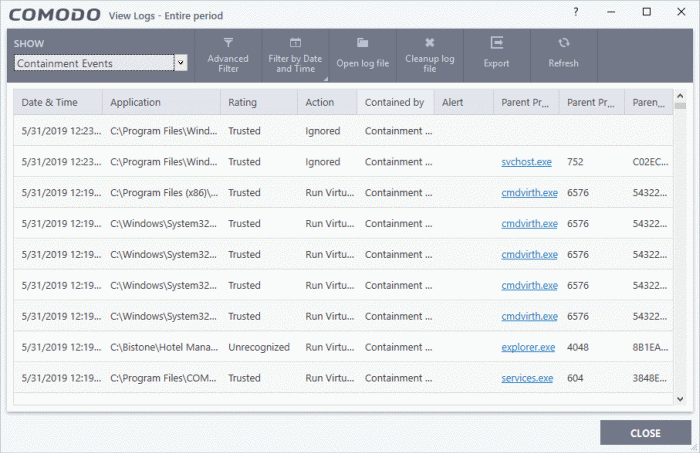
Date & Time - When the event occurred.
Application - The installation path of the application that was run in the container
Rating - The reputation of the contained application. The trust rating can be 'Trusted', 'Unrecognized' or 'Malicious'. Unrecognized files are run in the container until such time as they can be classified as 'Trusted' or 'Malicious'.
Action - How the malware was handled by CCS. This is also the restriction level imposed on the application by the container.
Contained by - The CCS service, policy or user that placed the application in the container.
Alert - Click 'Related Alert' to view the notification generated by the event
Parent Process - The program which spawned the contained process.
- Click the name of the parent process to view the hierarchical order of processes
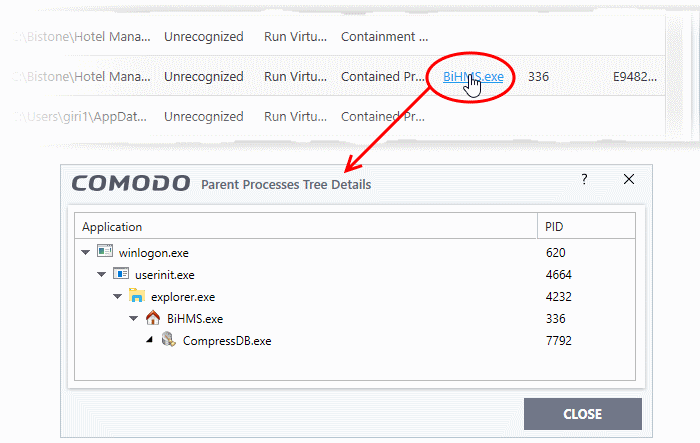
Parent Process ID - The unique identifier that points to the process
Parent process hash - The SHA1 hash value of the program which spawned the contained process.
- Click any column header to sort the entries in ascending \ descending order.
Website filtering
- Click 'Logs' in the CCS menu bar
- Select 'Website Filtering Events' from the drop-down at upper-left
Website filter logs are a record of all sites blocked (or allowed) by CCS. The logs record all attempts made by users to access blocked or allowed websites.
|
Background Note:
You can create filtering rules for specific users in 'Advanced Settings' > 'Website Filtering'.
|

Date & Time - When the event occurred.
Website - The URL of the site that was blocked, or allowed.
Category - The genre of the website. Example categories include 'Shopping sites', 'Social Media', 'Boutiques' etc. You can manage categories in 'Advanced Settings' > 'Website Filtering'.
Action - How the filter reacted to the connection attempt. For example, whether the attempt was allowed, blocked or an alert shown to the user.
- Click any column header to sort the entries in ascending \ descending order.
Device control
- Click 'Logs' in the CCS menu bar
- Select 'Device Control Events' from the 'Show' drop-down
Device control logs record events related to external devices. External devices include USB, optical, and storage drives plugged into your computer.
Events logged include:
- Files copied, deleted and moved
- Device enabled/disabled ('Log detected devices' must be enabled)
FYI - Admins can also configure device control in an Endpoint Manager profile. For example, if you want to allow unfettered access to certain devices you can (i) disable device control entirely (ii) remove the device class from the list of controlled types, or (iii) add specific devices to exclusions.
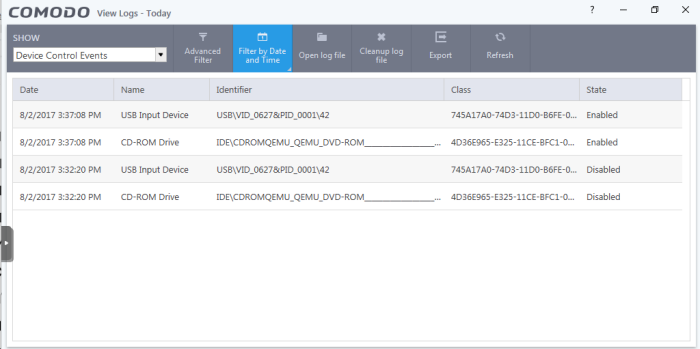
Date - When the event occurred.
Name - The type of device associated with the event.
Identifier - The identification string of the device
Class - The GUID (Globally Unique Identifier) string of the category of the device as defined by the Windows operating system.
State - Whether the device was allowed or blocked.
- Click any column header to sort the entries in ascending \ descending order
Autorun events
- Click 'Logs' in the CCS menu bar
- Select 'Autorun Events' from the drop-down at upper-left
Autorun logs show events where changes were attempted on Windows services, auto-start entries and scheduled tasks.
|
Background:
CCS monitors changes to registry items related to Windows Services, Autorun entries and scheduled tasks.
You can define the response CCS should take against unrecognized autoruns in 'Advanced Settings' > 'Advanced Protection' > 'Miscellaneous'.
You can also define the response to unknown autoruns found by an antivirus scan.
|
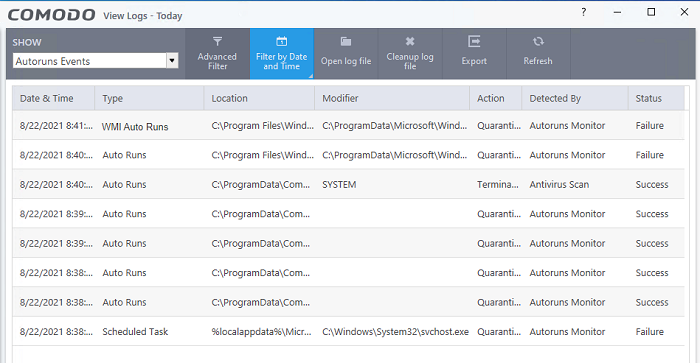
Date & Time - When the event occurred.
Type - Whether the detected item is an autorun entry, Windows service, or scheduled task.
Location - The installation path of the affected item, or the location of the new item
Modifier - The location of the application that made the change.
Action - How CCS responded to the event.
Detected By - Place where the scan was executed and runned
Status - Whether the action taken was a success or failure
- Click any column header to sort the entries in ascending \ descending order
Alerts displayed
- Click 'Logs' in the CCS menu bar
- Select 'Alerts' from the drop-down at upper-left
Alert logs are a record of all threat notifications generated by CCS, and also record the user's response to the alert.
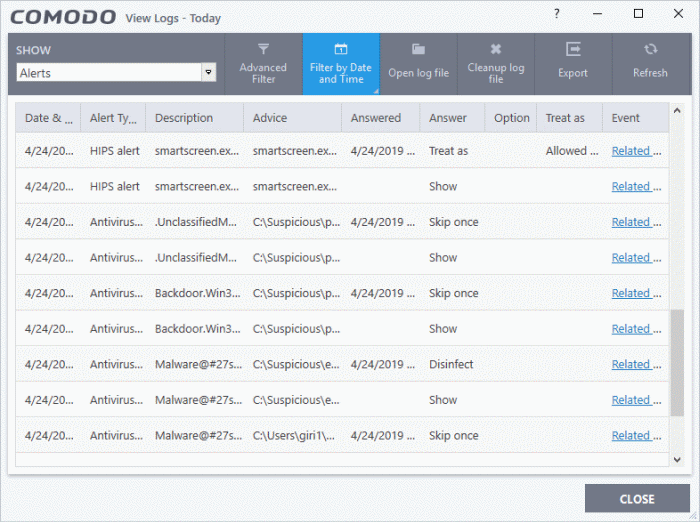
Date & Time - When the event occurred.
Alert Type - The security module that generated the alert. Alert types include antivirus, firewall, HIPS, containment, VirusScope and secure shopping.
Description - Name of the file or event that caused the alert.
Advice -The recommendation, or informational text in the alert. This text is intended to help users decide to respond to the threat.
Answered - Whether or not the alert was answered by the user. You will see the date and time of the response if an answer was provided.
Answer - The user's response to the alert. For example, 'Allow', 'Block', 'Disinfect', 'Skip'.
Option - Additional settings chosen by the user at the alert. For example, 'Remember My Answer'.
Treat As - Whether or not the user applied a specific ruleset to the file at the alert. The ruleset tells CCS the restriction level to apply to the file in future. Example rulesets include 'Treat as a safe application, or 'Treat as an installer'.
Event - Click 'Related Event' to view more details about the incident that triggered the alert.
- Click any column header to sort the entries in ascending / descending order.
Tasks launched
- Click 'Logs' in the CCS menu bar
- Select 'Tasks' in the drop-down at upper-left
A task log is a record of a CCS operation such as a virus scan or database update. The task log area shows all tasks run, their completion status, and other details.
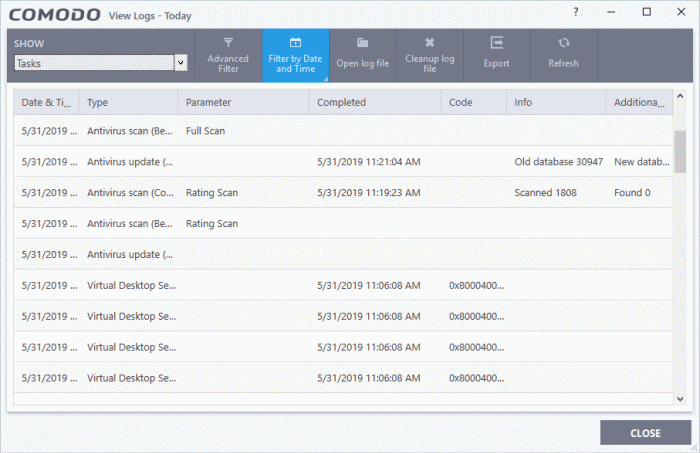
Date & Time - When the event occurred.
Type - The task that was performed. For example, 'Antivirus scan', or 'Database update'.
Parameter:
- The sub-type of the operation. For example, 'Quick Scan' is a sub-type of 'Antivirus scan'.
OR
- The target of the operation. For example, 'C:\Program Files' is the target area scanned.
Completed - The time that the operation finished
Code - Error code generated by Windows for CCS tasks that were not successful. No code is shown if the task finished successfully.
Info and additional info - Shows further details about the task. For update tasks, these fields show the old and new version numbers. For scan tasks, they show the number of items scanned and the number of viruses found.
- Click any column header to sort the entries in ascending \ descending order.
File List settings changes
- Click 'Logs' in the CCS menu bar
- Select 'File List Changes' in the drop-down at upper-left
The file list is an inventory of executables and applications on your computer. The list shows the file name, vendor, the date the file was discovered, and the file's trust rating.
- You can view the file list in CCS at 'Settings' > 'File Rating' > 'File List'.
File list logs are a record of any modifications to these files. Logged actions include adding a new file, removing a file, or changing the trust rating of a file.
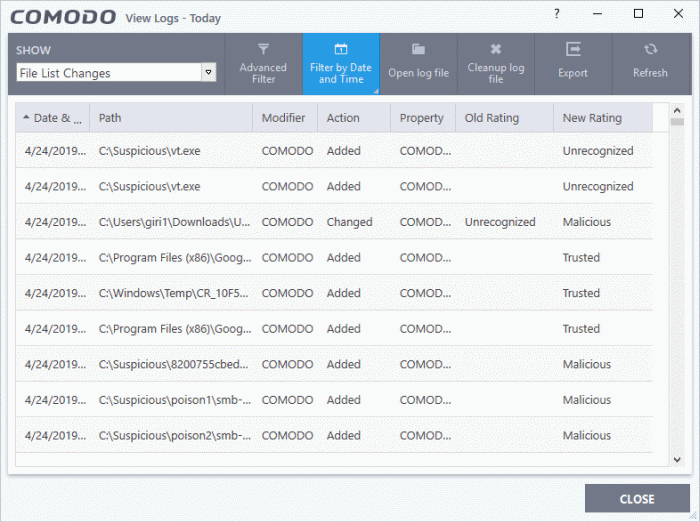
Date & Time - When the event occurred.
Path - The location or the SHA 1 hash value of the file that was changed.
Modifier - The service or user that made the change.
Action - Whether the file was added, removed, or assigned a new rating
Property - Whether the current trust rating was assigned by Comodo, an administrator, or a user.
Old Rating - The trust rating of the file before the change.
- The rating can be 'Trusted', 'Unrecognized' or 'Malicious'. Under default settings, unrecognized files are run in the container until Comodo classifies them as 'Trusted' or 'Malicious'.
New Rating - The trust rating of the file after the change.
- Click any column header to sort the entries in ascending \ descending order.
Vendors List changes
- Click 'Logs' in the CCS menu bar
- Select 'Vendor List Changes' in the drop-down at upper-left
CCS ships with a list of trusted vendors who have a reputation for creating legitimate, safe software. CCS allows unknown files which are digitally signed by one of these trusted vendors to run. Click 'Settings' > 'File Rating' > 'Vendor List' to view the list.
- You can also add new vendors, and change the rating of existing vendors. Admin / User ratings supersede the Comodo rating.
- The files published by these vendors are rated depending on the current rating assigned to the vendor
- Any changes to vendors in the list are logged in 'Vendor List Changes'
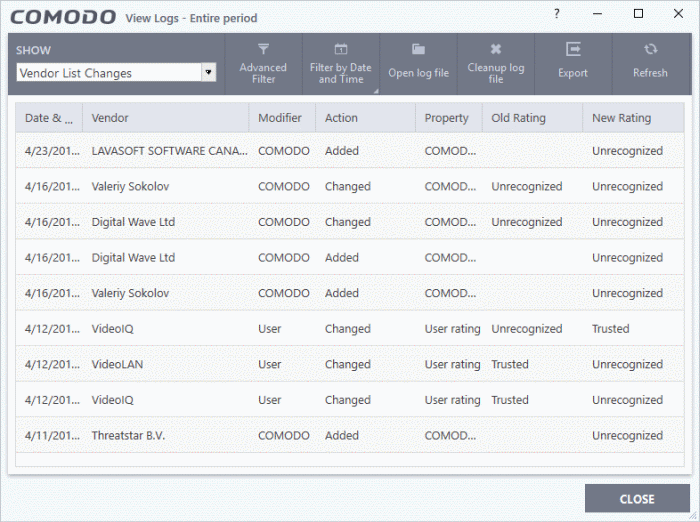
Date & Time - When the change event occurred.
Vendor - The name of the software publisher
Modifier - Who made the change (User or Comodo).
Action - Whether the vendor was added, removed, or assigned a new rating
Property - Whether the current rating was assigned by Comodo, an admin, or a user.
Old Rating - The trust rating of the vendor before the change.
- The rating can be 'Trusted', 'Unrecognized' or 'Malicious'. Under default settings, unrecognized files are run in the container until Comodo classifies them as 'Trusted' or 'Malicious'.
New Rating - The trust rating of the vendor after the change.
- Click any column header to sort the entries in ascending \ descending order.
Configuration changes
- Click 'Logs' in the CCS menu bar
- Select 'Configuration Changes' in the drop-down at upper-left
Configuration change logs are a record of locally made changes to CCS settings
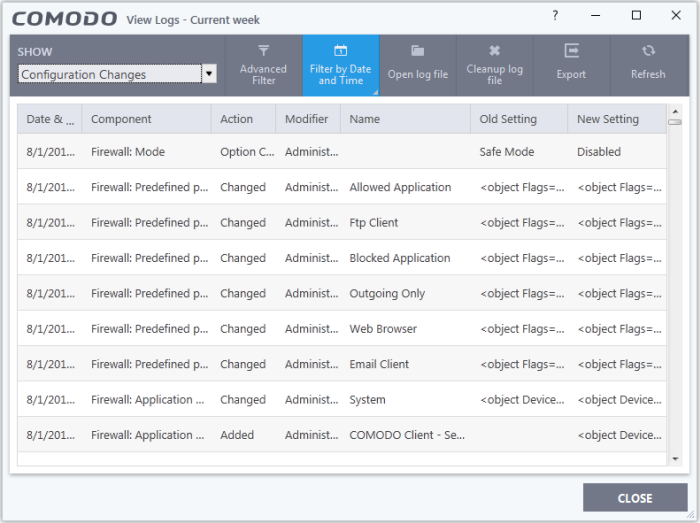
Date & Time - When the configuration change was done.
Component - The CCS interface that was modified.
Action - Short description of the change made to the CCS component. For example, if a setting was changed, or an exclusion was created.
Modifier - The service or user that made the change. Possible modifiers include 'User', 'Antivirus Alert', 'Auto-Learn', 'Firewall Alert', 'HIPS Alert', 'Containment Alert', 'Scheduler' and 'Comodo'.
Name - The item featured in the modification. This will vary depending on the component.
Old Setting - The value before the configuration change.
New Setting - The value after the configuration change.
- Pace your mouse over an entry in the 'Old Value' or 'New Value' column to view the full setting string
- Click any column header to sort the entries in ascending \ descending order.
Virtual Desktop events
- Click 'Logs' in the CCS menu bar
- Select 'Virtual Desktop Events' in the drop-down at upper-left
CCS records all events from the virtual desktop. Events that are recorded include:
- Launch and close the virtual desktop
- Pause, resume, and terminate a virtual desktop session
- Switch between the virtual desktop and the host desktop
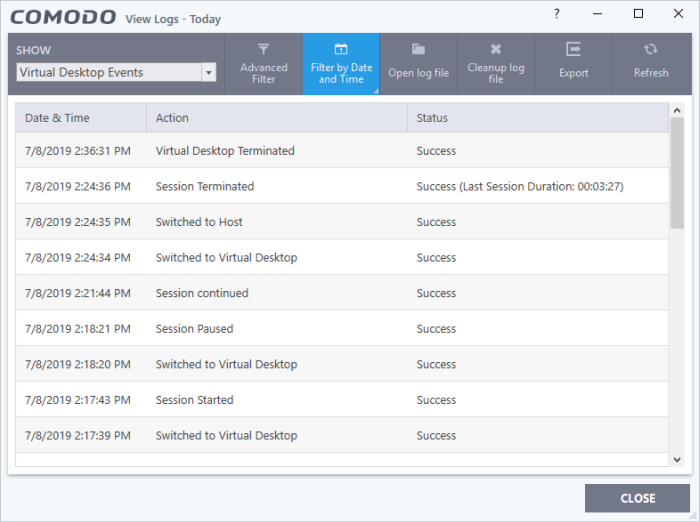
Date & Time - When the event occurred
Action - The operation executed
Status - Whether the action taken was a success or failure
- Click any column header to sort the entries in ascending \ descending order
Data Loss Prevention events
- Click 'Logs' in the CCS menu bar
- Select 'Data Loss Prevention Events' in the drop-down at top-left
The logs show items flagged by data loss prevention discovery scans and monitoring events:
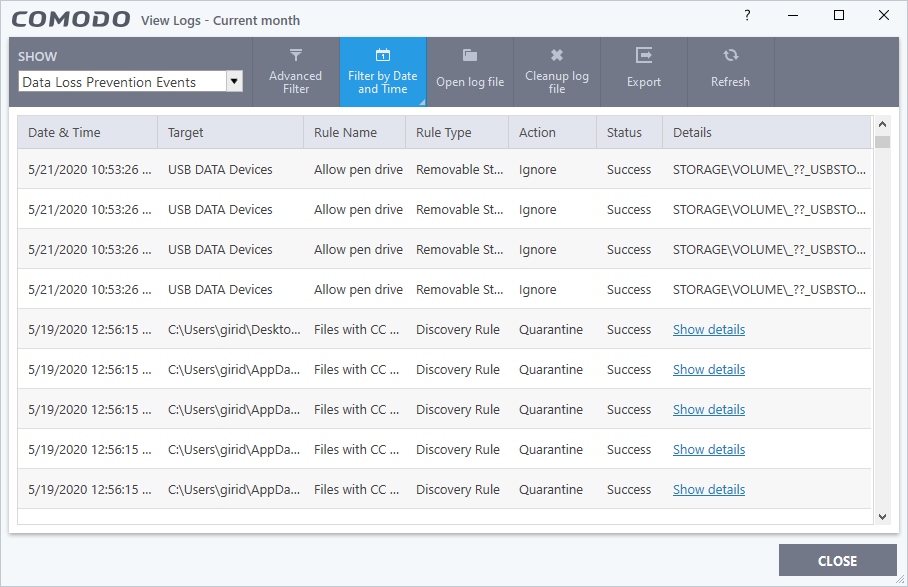
Date & Time - When the event occurred.
Target - The item affected by the rule.
Rule Name - The DLP rule that found the target item. This could be a DLP discovery rule or a monitoring rule.
Rule Type – Whether rule is a DLP discovery rule or a removable storage rule.
Action - How the file was handled in the DLP event.
Status - Shows whether the rule executed successfully or not.
Details - The specifics of the data found.
- DLP monitoring rule – Shows the removable storage device affected by the rule.
- DLP Discovery rule - Has a ‘Show details’ link which opens the specifics of the event. See View details of a file for more details.
View file details
- Click the 'Show details' column shows different information depending on the type of DLP event:
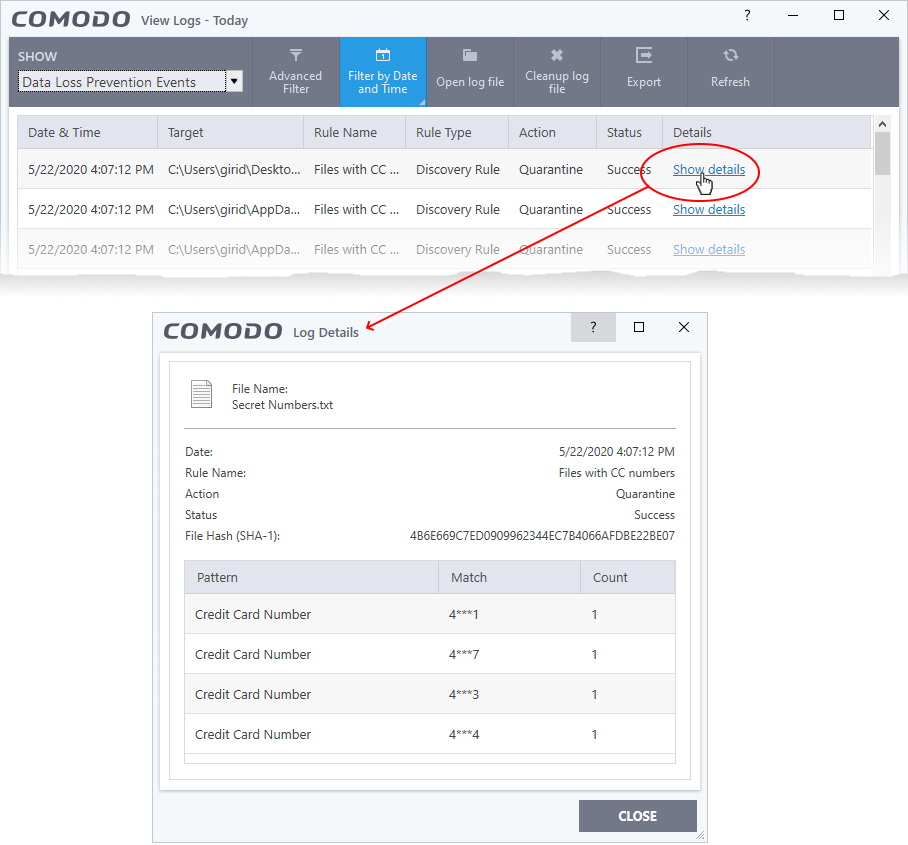
The screen shows the name of the file, and the rule/pattern which discovered sensitive data in the file.
The 'match' column shows the first and last characters of the actual discovered data. The option to show this should be enabled in the discovery rule.
Search and filter logs
You can run a simple filter of events by date, and use advanced filters to conduct more complex searches.
Filter by date/time
- Click 'Logs' in the CCS menu bar
- Select an event category from the drop-down at top-left
- Click 'Filter by Date and Time' to choose a specific period:
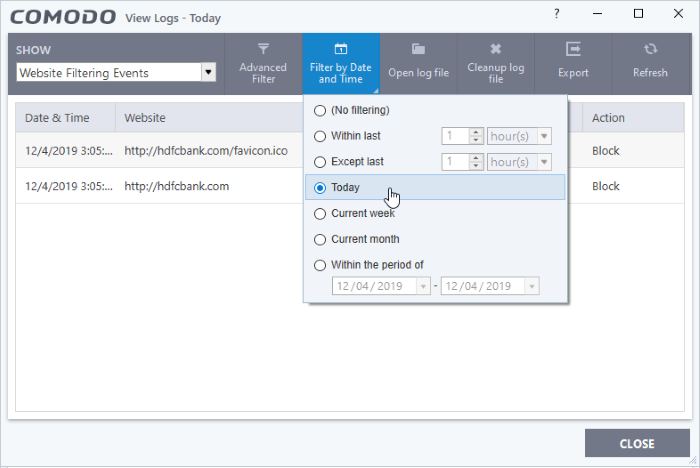
No filtering - Show every event logged since CCS was installed. If you have cleared the logs since installation, this option shows all logs created since that clearance.
Within last - Show all logs from a certain point in the past until the present time.
Except last - Exclude all logs from a certain point in the past until the present time.
Today - Show all events logged today, from 12:00 am to the current time. (Default)
Current Week - Show all events logged from the previous Sunday to today.
Current Month - Display all events logged from 1st of the current month to today.
Within the period of - Show logs between a custom date range.
You can also right-click inside the log viewer module and choose the time period.
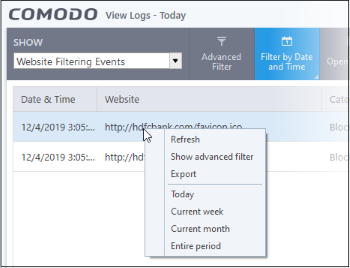
Advanced Filters
Advanced filters let you run complex queries based on a variety of criteria. Search parameters vary from module to module.
- Click 'Logs' in the CCS menu bar
- Select a module in the drop-down on the left
- Click 'Advanced Filter':
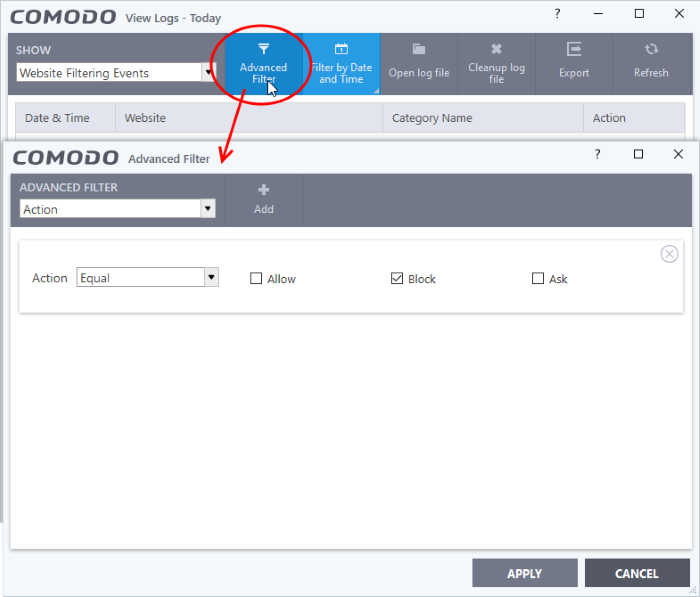
- Select a filter category at top-left then click 'Add'
- Search parameters vary according to the filter category. You can include multiple filter categories to refine your search.
Click the following links to view the options available with each module:
Antivirus Events
| Filter Category |
Description |
Parameters |
|
Action
|
Filter logs based on the action taken by CCS against the detected threat.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice. |
Select the filter parameter:
- Quarantine: Shows events at which the user chose to quarantine a file
- Remove: Shows events at which the user chose to delete the detected threat
- Ignore: Shows events at which the user chose to ignore the detected threat
- Detect: Shows events involving only the detection of malware
- Ask: Displays events where an alert was shown to the user so they could choose an action against a piece of detected malware
- Restore: Shows events at which quarantined applications were restored to original location by admin from Endpoint Manager
- Block: Shows events where suspicious applications were stopped
- Reverse: Shows events where VirusScope overrode potentially malicious actions
- False positive: Shows events where files flagged as threats by CCS were submitted to Comodo by the user as a false positive.
- Add To exclusions: Shows events in which the user chose to add an item to antivirus exclusions
- Add To trusted files: Shows events in which the user changed the file rating to 'Trusted'
- Restore from Quarantine: Shows events in which files were returned to original location from quarantine
- Delete from Quarantine: Shows events in which files were removed permanently from quarantine
|
| Location |
Filter the log entries related to events logged from a specific location. |
Enter the text or word that needs to be filtered
For example, if you select 'Contains' option from the drop-down and enter the phrase 'C:/Program Files/' in the text field, then all events containing the entry 'C:/Program Files/' in the 'Location' field are displayed. |
| Malware Name |
Filter the log entries related to specific malware. |
Enter the text in the name of the malware that needs to be filtered.
For example, if you choose 'Contains' from the drop-down and type 'siins' in the text field, then all events with 'siins' in the 'Malware Name' field are shown. |
| Status |
Filter the log entries based on the success or failure of the action taken against the threat by CCS.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
- Success: Shows events in which the actions against the detected threat were successfully executed (for example, the malware was successfully quarantined)
Failure: Shows events at which the actions against the detected threat failed to execute (for example, the malware was not disinfected) |
Virusscope events
| Filter Category |
Description |
Parameters |
|
Action
|
Filter logs based on the action taken by CCS against the detected threat.
|
Select the filter parameter:
- Quarantine: Shows events at which the user chose to quarantine a file
- Remove: Shows events at which the user chose to delete the detected threat
- Ignore: Shows events at which the user chose to ignore the detected threat
- Detect: Shows events involving only the detection of malware
- Ask: Displays events where an alert was shown to the user so they could choose an action against a piece of detected malware
- Restore: Shows events at which quarantined applications were restored to original location by admin from Endpoint Manager
- Block: Shows events where suspicious applications were stopped
- Reverse: Shows events where VirusScope overrode potentially malicious actions
- False positive: Shows events where files flagged as threats by CCS were submitted to Comodo by the user as a false positive.
- Add To exclusions: Shows events in which the user chose to add an item to antivirus exclusions
- Add To trusted files: Shows events in which the user changed the file rating to 'Trusted'
- Restore from Quarantine: Shows events in which files were returned to original location from quarantine
- Delete from Quarantine: Shows events in which files were removed permanently from quarantine
|
| Location |
Filter the log entries related to events logged from a specific location. |
Enter the text or word that needs to be filtered
For example, if you select 'Contains' option from the drop-down and enter the phrase 'C:/Program Files/' in the text field, then all events containing the entry 'C:/Program Files/' in the 'Location' field are displayed. |
| Malware Name |
Filter the log entries related to specific malware. |
Enter the text in the name of the malware that needs to be filtered.
For example, if you choose 'Contains' from the drop-down and type 'siins' in the text field, then all events with 'siins' in the 'Malware Name' field are shown. |
| Status |
Filter the log entries based on the success or failure of the action taken against the threat by CCS.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
- Success: Shows events in which the actions against the detected threat were successfully executed (for example, the malware was successfully quarantined)
Failure: Shows events at which the actions against the detected threat failed to execute (for example, the malware was not disinfected) |
Firewall Events
| Filter Category |
Description |
Parameters |
| Action |
Filter logs based on events according to the response (or action taken) by the firewall.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
- Blocked: Shows events where CCS prevented the connection
- Allowed: Shows events where the connection was allowed to proceed
Asked: Shows events where an alert was shown to the users so they could choose whether or not to allow the connection |
| Application |
Filter logs based on events propagated by a specific application |
Enter the text or word that needs to be filtered.
For example, if you choose 'Contains' from and enter the phrase 'cuckoo' in the text field, then all FW events containing the entry 'cuckoo' in the 'Application' column are displayed |
| Destination IP |
Filter logs based on events with a specific target IP address
Select 'Equal' or 'Not Equal' option from the drop-down box. 'Not Equal' will invert your selected choice.
Select 'IPv4' or 'IPv6' from the drop-down box.
|
Enter the IP address of the destination server or host, to filter the events that involve the connection attempts from/to that destination server or host.
For example, if you choose 'Contains' option from the drop-down, select IPv4 and enter 192.168.111.11 in the text field, then all events containing the entry '192.168.111.11' in the 'Destination IP' column will be displayed. |
| Destination Port |
Filter logs based on events that involved a specific target port number
|
Enter the destination port number in the text entry field
|
| Filter Category |
Descriptions |
Parameters |
| |
|
Filter logs based on events that involved a specific target port number
Select any one of the option the drop-down:
- Equal
- Greater than
- Greater than or Equal
- Less than
- Less than or Equal
- Not Equal
|
|
For example, if you choose 'Equal' option from the drop-down and enter 8080 in the text field, then all events containing the entry '8080' in the 'Destination Port' column will be displayed. |
| Direction |
Filter logs based on events of inbound or outbound nature.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
- In: Shows a list of events involving inbound connection attempts
- Out: Shows a list of events involving outbound connection attempts
For example, if you choose 'Equal' option from the drop-down and select the 'In' checkbox, then all inbound connection attempts will be displayed. |
| Protocol |
Filter logs based on events that involved a specific protocol.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
- TCP
- UDP
- ICMP
- IPV4
- IGMP
- GGP
- PUP
- IDP
- IPV6
- ICMPV6
- ND
For example, if you choose 'Equal' option from the drop-down and select the 'TCP' checkbox, then all connection attempts involving TCP protocol will be displayed. |
| Source IP |
Filter logs based on events that originated from a specific IP address
Select 'Equal' or 'Not Equal' option from the drop-down box. 'Not Equal' will invert your selected choice.
Select 'IPv4' or 'IPv6' from the drop-down box. |
Enter the IP address of the source server or host, to filter the events that involve the connection attempts from/to that source server or host system.
For example, if you choose 'Contains' then select IPv4 and enter 192.168.111.22 in the text field, then all events containing the entry '192.168.111.11' in the 'Source IP' column will be displayed. |
| Source Port |
Filter logs based on events that involved a specific source port number
Select any one of the option the drop-down:
- Equal
- Greater than
- Greater than or Equal
- Less than
- Less than or Equal
Not Equal |
Enter the destination port number in the text entry field
For example, if you choose 'Equal' and enter 8080 in the text field, then all events containing the entry '8080' in the 'Source Port' column will be displayed. |
HIPS Event
| Filter Category |
Description |
Parameters |
| Application |
Filter logs based on events propagated by a specific application |
Enter the search criteria for filtering the logs in the text field.
For example, if you choose 'Contains' from the drop-down and enter the phrase 'cuckoo' in the text field, then all events containing the entry 'cuckoo' in the 'Application' column are displayed. |
| Action |
Filter logs based on events according to the response (or action taken) by HIPS
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice. |
Select the filter parameter:
- Scanned online and found malicious
- Access memory
- Create process
- Terminate process
- Modify key
- Modify file
- Direct memory access
- Direct disk access
- Direct keyboard access
- Direct monitor access
- Load driver
- Send message
- Install Hook
- Access COM interface
- Execute image
- DNS/RPC client access
- Change HIPS Mode
- Shellcode injection
- Block file
- Suspicious
- Hook
- Alert Suppressed
- Scanned and found safe
For example, if you choose 'Equal' and select 'Create process', only events involving the creation of a process by applications are displayed. |
| Target |
Filter logs based on events that involved a specified target application. |
Enter the search criteria for filtering the logs in the text field.
For example, if you choose 'Contains' and enter the phrase 'svchost.exe' in the text field, then all e |
Containment Events
| Filter Category |
Description |
Parameters |
| Application |
Show events propagated by a specific application. |
Enter the search criteria for filtering the logs in the text field.
For example, if you choose 'Contains' and enter the phrase 'pcflank' in the text field, then all events containing the entry 'pcflank' in the 'Application' column are displayed. |
| Rating |
Show events which concern files that have a specific trust-rating.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice. |
Select the filter parameter:
- None
- Unrecognized
- Trusted
- Malicious
For example, if you choose 'Equal' and select the 'Unrecognized' file rating, only the containment events involving applications that are categorized as 'Unrecognized' are displayed. |
| Action |
Show events where a specific action was applied to the file by CCS
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the restriction level(s) applied by the container to the applications, either automatically of or chosen by the user from the alert.
- Run Restricted
- Run Virtually
- Blocked
- Ignored
For example, if you choose 'Equal' from the drop-down and select 'Run Virtually', only the events of applications that are run inside the container are displayed. |
| Contained by |
Show events where the file was isolated by a specific module or user
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' will invert your selected choice.
|
Select the source(s) by which the applications were contained.
- Containment Policy
- User
- Contained Process
- Containment Service
For example, if you choose 'Contains' and select the 'User' checkbox, then only events involving applications that were manually run inside the container are displayed.
|
| Parent Process |
Show files contained based on its source process |
Enter the name of the application associated with the process, that launched contained item as the search criteria for filtering the logs in the text field.
For example, if you choose 'Contains' and enter the phrase 'RuntimeBroker.exe' in the text field, then all events containing the entry 'RuntimeBroker.exe' in the 'Parent Process' column are displayed. |
| Parent Process ID |
Show events created by a source process ID
Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
Enter the process ID of the application associated, that launched contained item as the search criteria for filtering the logs in the text field.
For example, if you choose 'Contains' and enter the ID '2612' in the text field, then all events containing the entry '2612' in the 'Parent Process ID' column will be displayed. |
| Parent Process Hash |
Show events where items was contained based on its source process(es) specified by hash value(s) of executable file(s) associated with the source process(es)
Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
Enter the SHA1 hash value of the executable file associated with the process, that launched contained item as the search criteria. |
Website Filtering Events
| Filter Category |
Description |
Parameters |
| Website |
Show only events that involved a specific website
Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
Enter the website address in part or full, to filter the logs involving the website.
For example, if you choose 'Contains' option from the drop-down and enter the phrase 'facebook.com' in the text field, then all events that involve the website 'facebook.com' in the 'Website' column are displayed. |
| Category Name |
Show events that involved websites which are covered by a website filtering category.
|
Enter the website filter category name, to filter the logs involving the category
For example, if you choose 'Contains' and enter the phrase 'Malware Sites' in the text field, then all events involving websites in the 'Malware Sites' category are displayed. |
| Action |
Show only events that involved a specific response by CCS
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the action(s) to filter the logs involving those action(s).
For example, if you choose 'Equal' and 'Block', then only events where websites blocked are displayed. |
Device Control Events
| Filter Category |
Description |
Parameters |
| Name |
Filter the entries based on the type of the device. |
Enter the type of the device in full or part as your filter criteria in the text field.
For example, if you choose 'Contains' and type 'USB Input Device' in the text field, you will see logs related to USB input devices like keyboards, mice and finger print scanners. |
| Identifier |
Filter entries based on the device ID of the external device. |
Enter the device ID of the device in full or part as your filter criteria in the text field.
For example if you have chosen 'Contains' and entered 'USB\VID_0627&PID_0001', in the text field only those log entries related to external devices whose device ID contains the string are displayed. |
| Class |
Filter the entries based on the GUID of the device |
Enter a Device Class ID (GUID) in part or full as your search criteria
For example, if you select 'Contains' option from the drop-down field and enter '4D36E967', then all events containing the entry '4D36E967' in the 'Class' field are displayed.. |
| State |
Filter events based on whether the device connection attempt was allowed or blocked. |
Select the parameter to refine your search.
Disabled |
Autorun Events
| Filter Category |
Description |
Parameters |
| Type |
Filter entries based on the class of autorun
Select 'Equal' or 'Not Equal' from the drop-down. 'Not Equal' will invert your choice |
Choose from:
- Windows Service
- Autostart entry
- Scheduled task
- WMI Autostart entry
|
| Location |
Filter entries based on the application path
Select the 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' will invert your selected choice. |
Enter the location or a part of it as your filter criteria in the text field.
For example, if you have chosen 'Contains' and entered 'C:/Program Files (x86)/Cuckoo Files/Cuckoo.exe in the text field, then only log entries with the same value in the 'Path' column are displayed. |
| Modifier |
Filter logs by the file or user that launched the event.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice. |
Enter the location or a part of it as your filter criteria in the text field.
For example if you choose 'Contains' and enter 'C:/Users/tester/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/UnknownAppUI3.exe' in the text field, then only log entries with the same value in the 'Path' column will be displayed. |
| Action |
Filter the events based on CCS response to the detected threat
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
- Ignore - CCS does not take any action
- Terminate - CCS stops the process / service
- Terminate and Disable - Auto-run processes will be stopped and the corresponding auto-run entry removed. In the case of a service, CCS disables the service.
Quarantine and Disable - Auto-run processes will be quarantined and the corresponding auto-run entry removed. In the case of a service, CCS disables the service. |
| Detected By |
Filter the entries based on the CCS component that discovered the threat
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice
|
Select the specific filter parameter to refine your search.
- Autorun monitor
- Antivirus Scan
|
| Status |
Filter the entries based on the success or failure of the action taken against the threat by CCS.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the specific filter parameter to refine your search.
- Success: Shows events where the actions against the detected threat were successful. For example, the malware was successfully quarantined.
- Failure: Shows events where the intended actions against the detected threat were not successful. For example, the malware was not disinfected.
|
Alerts
|
Filter Category
|
Description
|
Parameters
|
|
Advice
|
Filter entries by the security recommendation in the alert.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the text or word as your filter criteria.
For example, choose 'Contains' and enter the phrase 'you can safely allow this request' in the text field.
|
|
Answer
|
Filter the events based on what action the user selected at the alert.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the parameter to refine your search.
- Unknown
- Allow
- Deny
- Treat as
- Disinfect
- Quarantine
- Quarantine and reserve
- Skip once
- Add to exclusions
- Add to trusted files
- False positive
- Skip
- Terminate
- Keep inside the Container
- Run outside the Container
- Deny and Terminate
- Deny, Terminate and Reverse
- Containment
- Visit with Secure Browser
- Run Unlimited
- Run inside the Container
- Blocked
For example, if you choose 'Equal' from the drop-down and select the 'Add to exclusions' checkbox, only the alerts where you answered 'Ignore' > 'Ignore and Add to exclusions' are displayed.
|
|
Answered
|
Filter logs based on the date the user answered the alerts.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Enter or select the required date from the date picker
For example, if you select 'Equal' and select '07/31/2017', only alerts answered on 07/31/2017 are displayed.
|
|
Description
|
Filter the entries based on the description of the attempt displayed in the alert.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the text or word as your filter criteria.
For example, if you select 'Contains' from the drop-down and enter 'connect to the internet', only the log entries of firewall alerts that contain the phrase 'connect to the internet' in the description are displayed.
|
|
Option
|
Filter the log entries where the user selected an additional options like 'Remember my answer', 'Submit as False Positive' from the alert.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the specific filter parameters to refine your search.
- Remember
- Restore point
- Submit
- Trusted publisher
For example, if you choose 'Equal' from the drop-down and select 'Remember' from the checkbox options, only the log entries of alerts for which 'Remember my answer' option was selected are displayed.
|
|
Treat as
|
Filter events where the user chose specific actions on the alert. For example, 'treat as a safe application', 'treat as an installer' and so on.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the text or word as your filter criteria
For example, if you have chosen 'Contains' from the drop-down and entered 'Installer' in the text field, only the log entries containing the phrase 'Installer' in the 'Treat As' column are displayed.
|
|
Alert Type
|
Filter the log entries based on the CCS component that triggered the alert
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the specific filter parameters to refine your search.
- Antivirus Alert
- Firewall Alert
- HIPS alert
- Containment alert
- VirusScope Alert
- Network alert
For example, if you select 'Equal' from the drop-down and select 'Antivirus Alert' checkbox, only the log of antivirus alerts are displayed.
|
CCS Tasks
|
Filter Category
|
Description
|
Parameters
|
|
Code
|
Filter the entries based on specified error code
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Enter the code or a part of it as your filter criteria in the text field.
For example, if you have select 'Equal' and entered '0x80004004' in the text field, then only entries containing the value '0x80004004' in the 'Code' column are displayed.
|
|
Completed
|
Filter events based on tasks successfully finished on the specified date
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Enter or select the required date from the date picker
For example, if you choose 'Equal' and select '08/01/2019', only the logs of tasks completed on 08/01/2019' are displayed.
|
|
Parameter
|
Filter the entries based on the specified parameter. A 'parameter' is a sub-type of the main task type. For example, 'Quick Scan' and 'Rating Scan' are both parameters of the main task type 'Antivirus Scan'.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the text or word as your filter criteria.
For example, if you choose 'Contains' option from the drop-down and enter the phrase 'Quick Scan' in the text field, then only the entries of 'Antivirus Scan Tasks' with the scan parameter 'Quick Scan' are displayed.
|
|
Type
|
Filter the entries based on the CCS tasks category.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the specific filter parameters to refine your search.
- Antivirus update
- Antivirus scan
- Log Clearing
- Product upgrade
- Binary update
- File Rating DB Upgrade
- Purge file list
- Virtual Desktop Session
- Reset the Container
- DLP Discovery Scan
|
File List Changes
|
Filter Category
|
Description
|
Parameters
|
|
Location
|
Filter the entries based on the file path whose trust rating was changed
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the location or a part of it as your filter criteria in the text field.
For example if you have chosen 'Contains' and entered 'C:/Program Files (x86)/Cuckoo Files/Cuckoo.exe in the text field, then only log entries with the same value in the 'Path' column are displayed.
|
|
Modifier
|
Filter events based on who changed the file rating
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the filter parameter to refine your search
- Administrator
- User
- Comodo
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed.
|
|
Action
|
Filter the entries based on the file activity
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the filter parameter to refine your search
For example, if you select 'Equal' from the drop-down and select 'Removed' checkbox, only the logs of files that were removed from the file list are displayed.
|
|
Rating Source
|
Filter the entries by who provided the file rating
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Ratings can be provided by:
- Administrator
- Administrator (by Vendor)
- User
- User (by Vendor)
- AV database
- Trusted installer
- FLS
- FLS (by Vendor)
- Valkyrie
- SmartScreen
- Signed by Comodo
- Signed by Microsoft
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only the logs of files that were rated by the users are displayed.
|
|
Old Rating
|
Filter the entries based on trust rating of files before the change
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Select the filter parameter to refine your search
- Unrecognized
- Trusted
- Malicious
For example, if you select 'Contains' from the drop-down and select 'Unrecognized' checkbox, only the logs of files that are rated as 'Unrecognized' in the 'Old Rating' column are displayed.
|
|
New Rating
|
Filter logs by the trust rating of files after the change
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Select the filter parameter to refine your search
- Unrecognized
- Trusted
- Malicious
For example, if you select 'Contains' from the drop-down and select 'Malicious' checkbox, only the logs of files that are rated as 'Malicious' in the 'New Rating' column are displayed.
|
|
File Hash
|
Filter logs by hash value
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
- Enter the SHA1 hash value of the file in the text field to refine your search
|
Vendor List Changes
|
Filter Category
|
Description
|
Parameters
|
|
Vendor
|
Filter logs by the software publisher name whose trust rating was changed
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Type the name of the vendor in full or part in the text field.
For example if you choose 'Contains' and enter 'Digital' in the text field, only those log entries related to the vendors who has contain 'Digital' as a part in their name are displayed.
|
|
Modifier
|
Filter logs by who changed the vendor rating
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the filter parameter to refine your search
- Administrator
- User
- Comodo
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed.
|
|
Action
|
Filter logs by the type of change made to the vendor list.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Possible actions:
For example, if you select 'Equal' from the drop-down and select 'Removed' checkbox, only the logs of vendors that were removed from the vendor list are displayed.
|
|
Property
|
Filter logs by the entity that provided the vendor rating
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Entities that can provide trust ratings:
- Administrator Rating
- User Rating
- Comodo Rating
For example, if you select 'Equal' from the drop-down and select 'User Rating' checkbox, only the logs of vendors that were rated by users are displayed.
|
|
Old Rating
|
Filter logs by the trust rating of the vendor before the change
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Select the filter parameter to refine your search
- Unrecognized
- Trusted
- Malicious
For example, if you select 'Contains' from the drop-down and select 'Unrecognized' checkbox, only the logs of vendors that are rated as 'Unrecognized' in the 'Old Rating' column are displayed.
|
|
New Rating
|
Filter logs by the vendor's trust rating after the change.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Possible new trust ratings are:
- Unrecognized
- Trusted
- Malicious
For example, if you select 'Contains' from the drop-down and select 'Malicious' checkbox, only the logs of vendors that are rated as 'Malicious' in the 'New Rating' column are displayed.
|
Configuration Changes
|
Filter Category
|
Description
|
Parameters
|
|
Action
|
Filter logs by the type of change that was made. For example, rule modified, file exclusion created.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Options are:
- Added
- Changed
- Removed
- Option changed
|
|
Modifier
|
Filter events based on who changed the configuration such as the user, administrator and response given to an alert
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
The possible modifiers are:
- User
- Auto learn
- Antivirus Alert
- Firewall Alert
- HIPS alert
- Containment alert
- Scheduler
- Comodo
- Administrator
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed.
|
|
Name
|
Filter the entries based on object label that was affected by the configuration change, for example, Shared Spaces, Windows Management and so on
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the object name as filter criteria in the text box.
For example, if you choose 'Contains' then enter the phrase 'surfer.exe' in the text field, then you will only see logs with surfer.exe in the name column.
|
|
Component
|
Filter logs by the object modified by the action.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the affected object.
It is not possible to list all possible objects in this table. Please consult the list in the search interface.
|
Virtual Desktop Events
|
Filter Category
|
Description
|
Parameters
|
|
Action
|
Filter logs by the type of virtual desktop activity.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Possible activities:
- Virtual Desktop Launched
- Virtual Desktop Terminated
- Session Started
- Session Paused
- Session Continued
- Session Terminated
- Switched to Windows View
- Switched to Virtual Desktop
For example, if you select 'Equal' from the drop-down and select 'Session Started' checkbox, only the session initiated events are displayed in the 'Action' column.
|
|
Status
|
Filter logs by whether the event was was successful or not. Examples include paused sessions successfully resumed, wrong PIN entered and user could not resume a paused session.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Possible outcomes are:
|
Data Loss Prevention Events
|
Filter Category
|
Description
|
Parameters
|
|
Target
|
Filter entries by document location and / or storage device.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the location, or a part of it, as your filter criteria.
|
|
Rule
|
Filter entries by rule name
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice.
|
Enter the DLP rule name, or a part of it, as your filter criteria.
|
|
Action
|
Filter entries by the action taken on the target. The action may be:
1) An action CCS took on target a file.
2) An action that a user took on the target file.
3) An action CCS took on an external device.
|
- Ignore - CCS did not take any action on the file. You are, of course, free to review and assess the file.
- Quarantine - CCS moved the files to quarantine
- Restore from Quarantine - The file was moved back to its original location by the user
- Delete from Quarantine - The file was removed from the system by the user
- Blocked - CCS implemented 'Read-only' mode on an external device, preventing users from copying potentially sensitive files to it.
|
|
Status
|
Filter logs by whether the event was was successful or not.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Possible outcomes are:
|
Export the logs
The CCS log viewer lets you save the logs of a chosen module as an HTML file.
- Open CCS log viewer as explained above
- Choose the module from the drop-down at the top left
- Apply filters to choose which logs are to be included in the saved file. See above if you need help to apply filters.
- Click 'Export' on the top
- Alternatively, right-click inside the log viewer and choose 'Export' from the options
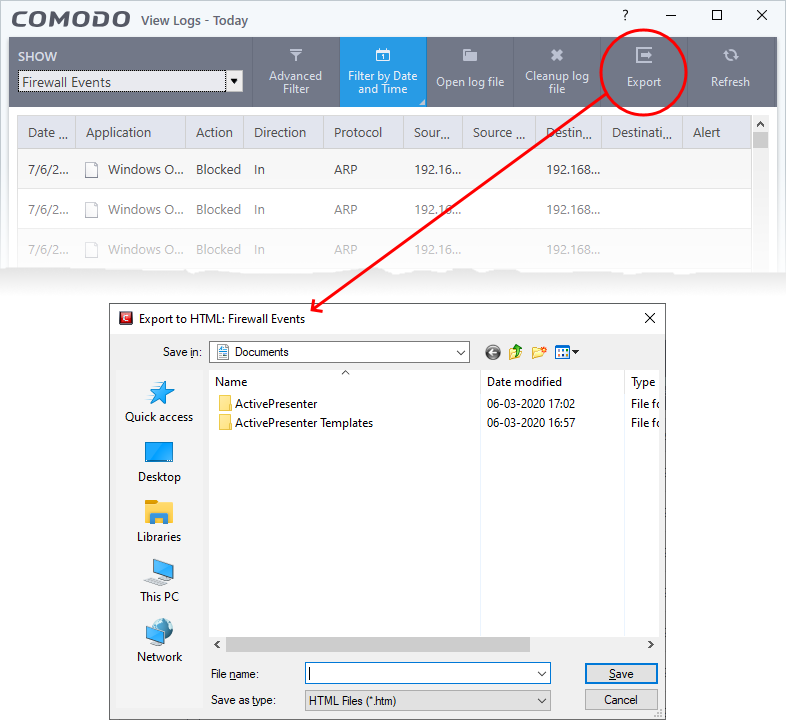
- Navigate to the location to save the HTML file, enter a name and click 'Save' to save the logs as HTML file.



























