-
The remote control (RC) application lets you take over Windows and Mac devices to solve issues, install third party software, and run system maintenance.
-
Once installed, you can start the application from the Endpoint Manager interface or direct from your desktop.
-
This tutorial explains how to:
Install and login to the application
-
Login to ITarian from your Windows or Mac OS device
-
Click ‘Applications’ > ‘Endpoint Manager’
-
Click ‘Devices’ > ‘Device List' > 'Device Management'
-
Select the device that you want to control
-
Click 'Remote Control'
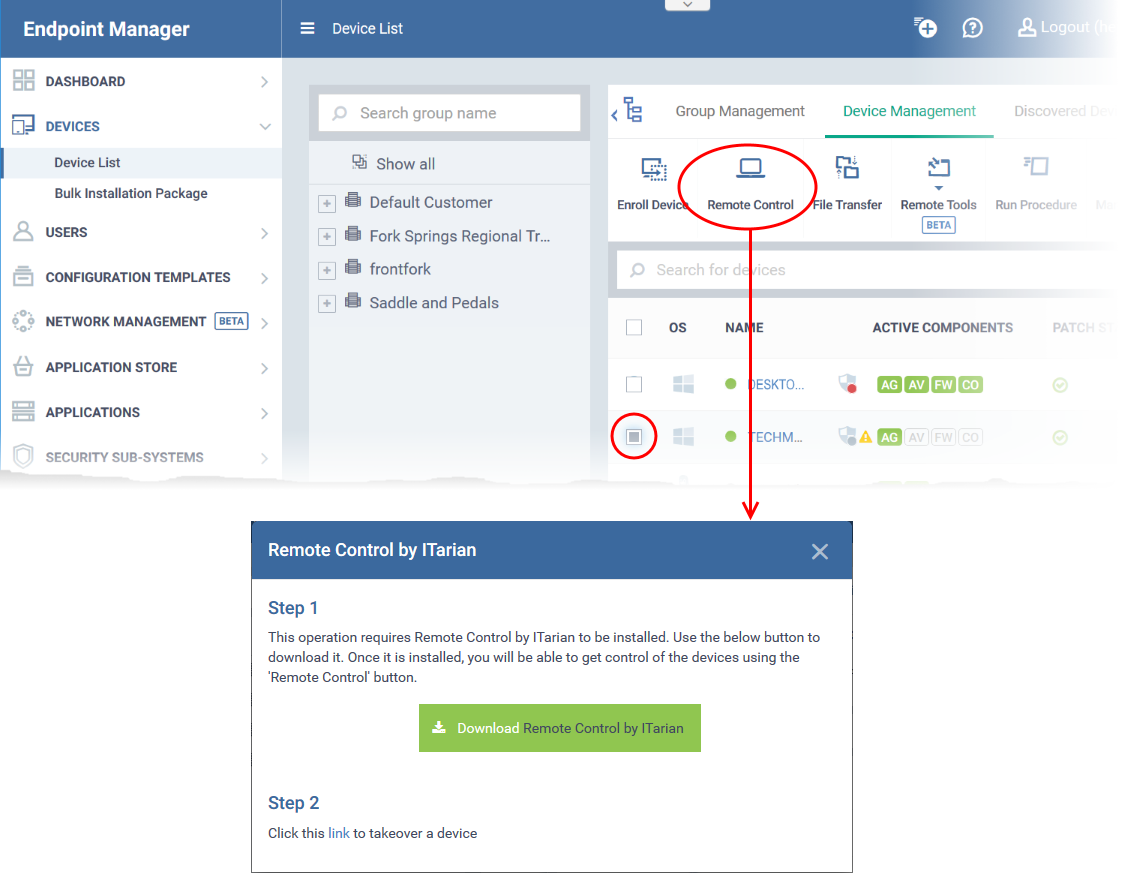
-
From this point forward, the application will automatically open when you click the ‘Remote Control’ button.
-
You can also open the application outside of Endpoint Manager by clicking the tray icon on your desktop.
-
Next, log-in to the remote control application with your username and password:
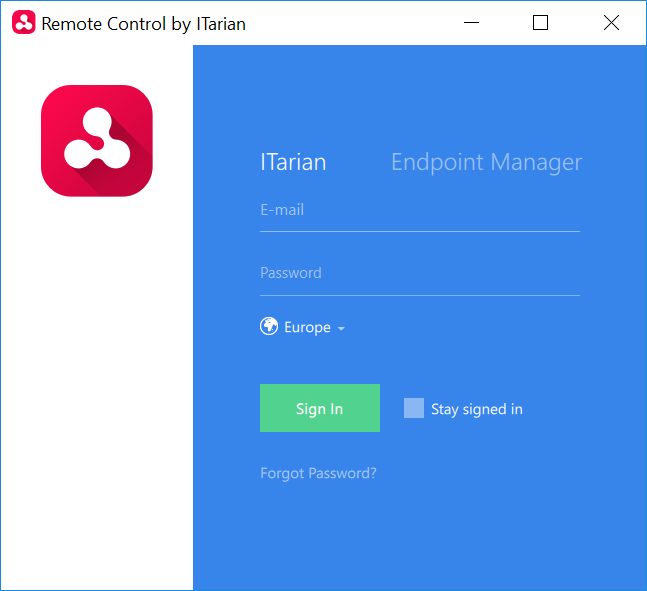
There are two ways you can login:
1. ITarian admins and technicians:
- Click the 'ITarian' tab
- Select your region
- Enter your ITarian account username and password
- Click 'Sign-in'
- If 'Two-Factor Authentication' is enabled for your account, then you have to enter the authentication code generated in the 'Google Authenticator' app on your mobile device. See this page for help to activate two factor authentication for your account, if you haven't done so.
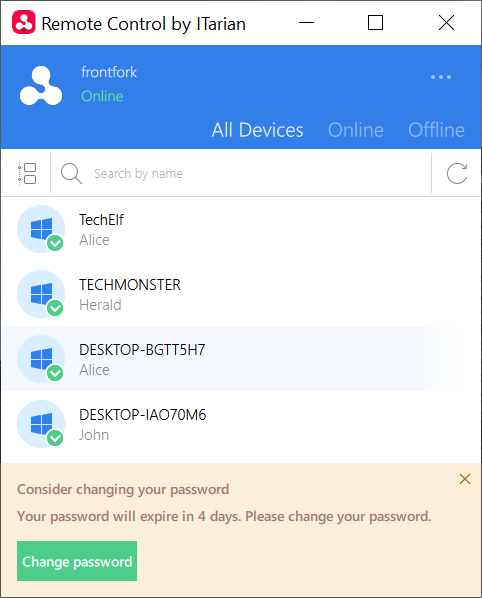
After login, the list of Windows and Mac OS devices added to your account is shown.
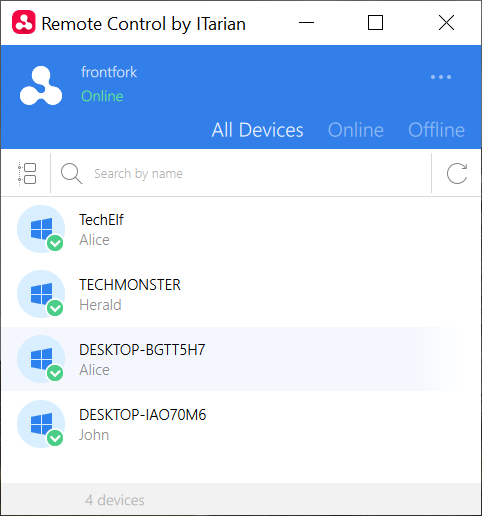
Next: Take control of a Windows or Mac OS device
2. Endpoint Manager admins
- Click the 'Endpoint Manager' tab
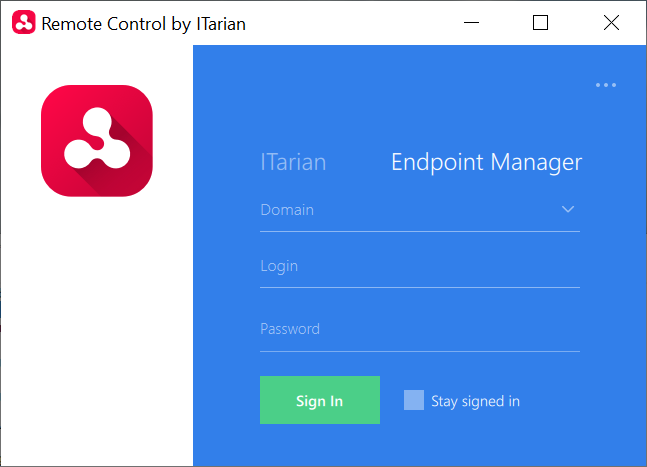
- Enter your Endpoint Manager domain. Your domain name is contained in the account activation mail sent to you. Usually, the domain name is of the format:
- For MSPs - <your company name>-msp.cmdm.comodo.com
- For Enterprise customers - <your company name>.cmdm.comodo.com
- Enter your username and password
- Click 'Sign In'
Take control of a Windows or Mac OS device
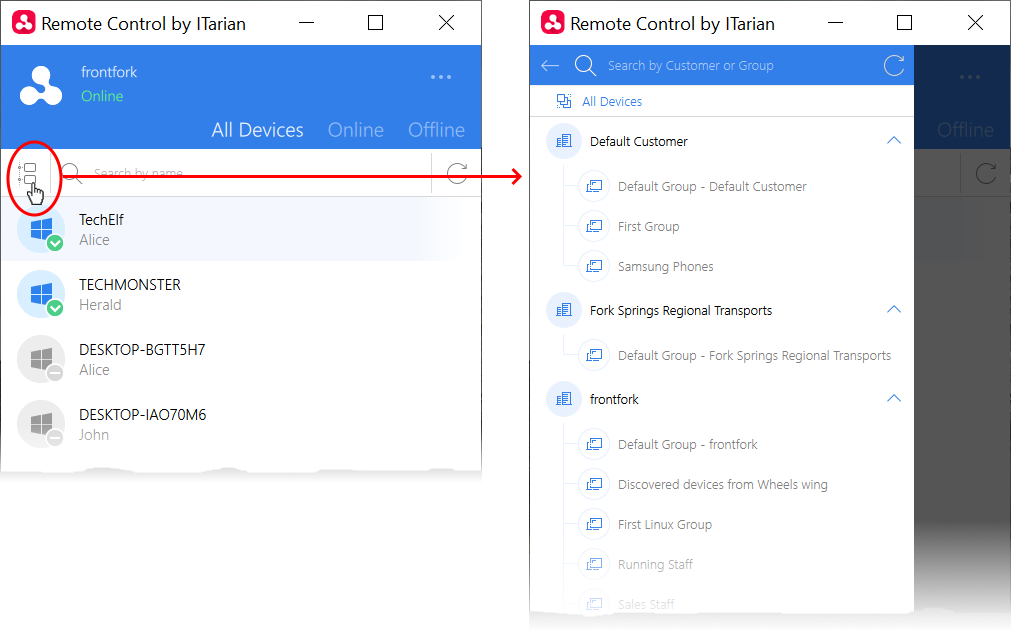
- Click the tree icon on the left to filter devices by company or device group:
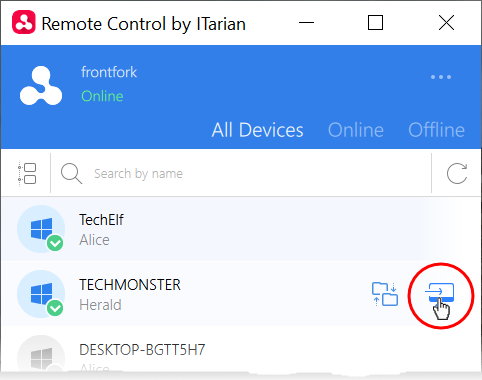
- Move your mouse over the device you want to control then click the 'desktop take over' icon on the right:
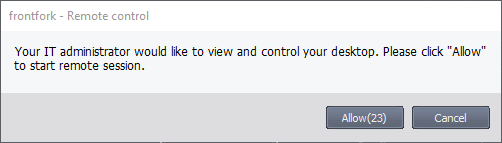
- A connection request is shown to the end-user if so configured in the device profile:
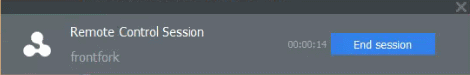
The following notification appears on the endpoint when you have established control:
You can now access the desktop of the remote computer:
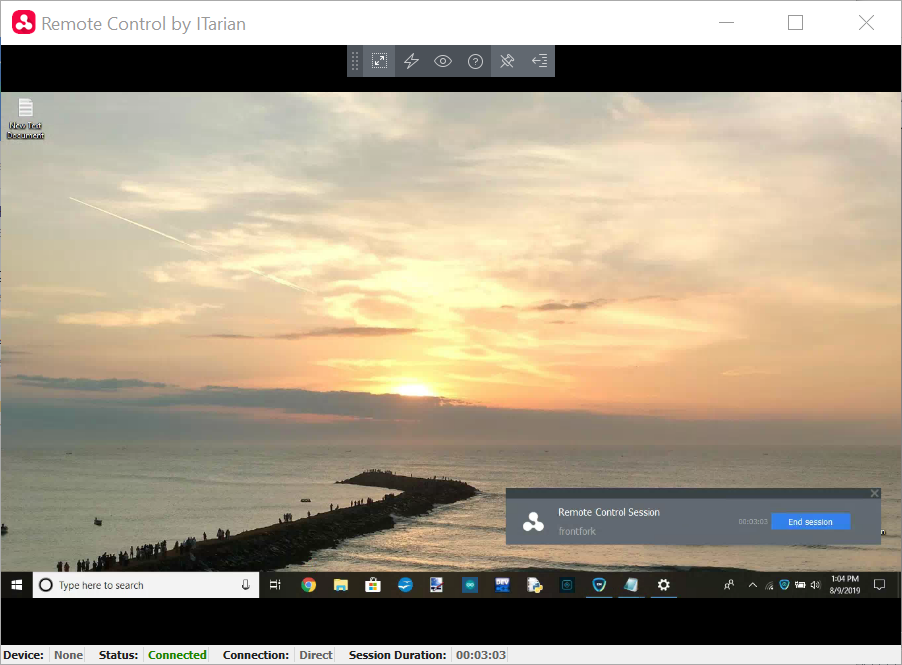
Use the application to perform operations on the remote device
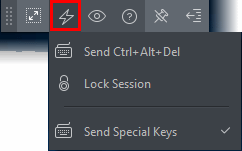
Special Key Combinations
|
Admin Device
|
Remote Device
|
|
Windows
|
Mac OS
|
|
Windows
|
'Windows' key is sent only to the remote device
Shortcuts in combination with 'Windows' key are applied only to the remote device
|
'Windows'/'Command' key is sent only to the remote device.
Exceptions:
Ctrl+Alt+Del
Win+L
PRINT SCREEN and NUMLOCK are not sent to the remote device
NumPad digit keys always behave as arrow-keys on Mac OS
'Context Menu' key is sent as zero scan code and appears as a key 'a'.
|
|
Mac OS
|
All shortcuts with the 'Command' key are applied to the remote device except 'Command+Esc’
Command+Tab - Switches between applications
F11 - Shows desktop
Ctrl +Up Arrow - Shows all Windows
Ctrl+Down Arrow - Shows active application Window
|
If Apple is keyboard used:
Media buttons (e.g. PLAY, STOP, MISSION CONTROL), POWER, EJECT keys and all system shortcuts with these keys are applied only to the local device.
Shortcuts with COMMAND are applied to the remote device, except 'COMMAND' key+Esc
Command+Tab - Switches between applications
Ctrl +Up Arrow - Shows all Windows
Ctrl+Down Arrow - Shows active application Window
Fn+F11 - Shows desktop
Fn+F12 - Shows Dashboard or enable standard key in Keyboard settings
If non-Apple keyboard is used:
Shortcuts with WIN are applied to the remote device, except 'WIN' key+Esc
Command+Tab - Switches between applications
Ctrl +Up Arrow - Shows all Windows
Ctrl+Down Arrow - Shows active application Window
F11 - Shows desktop
F12 - Shows Dashboard
|